Threat Modeling
Introduction
Threat modeling is an important resource for planning security requirements and understanding the risks that exist in a system (Department of Health and Human Services, 2020). This paper will examine three threat models for use in the healthcare industry. Specifically, it will summarize the STRIDE Model, the PASTA Model, and the OCTAVE Model and choose one to recommend to the organization’s CEO.
For the selected model, the paper will outline common security risks and corresponding severity levels in the context of the selected threat modeling framework. These risks will include topics such as user authentication and credentials with third-party applications. These scenarios will provide information for the CEO to be able to decide whether to accept the risks or mitigate them.
STRIDE Model
STRIDE stands for Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, and Elevation of Privileges (Department of Health and Human Services, 2020). Each letter of the acronym represents an area of security risk that the STRIDE model attempts to address (Department of Health and Human Services, 2020). As a point of reference, the Department of Health and Human Services (2020) identifies eight potential authentication threats and categorizes all but one into the “spoofing” category of risk. The remaining threat is categorized into the “Elevation of Privileges” category.
The STRIDE model begins by examining each component of your system, determining the risks associated with each component, and establishing risk mitigation strategies (Department of Health and Human Services, 2020). The following diagram demonstrates this.
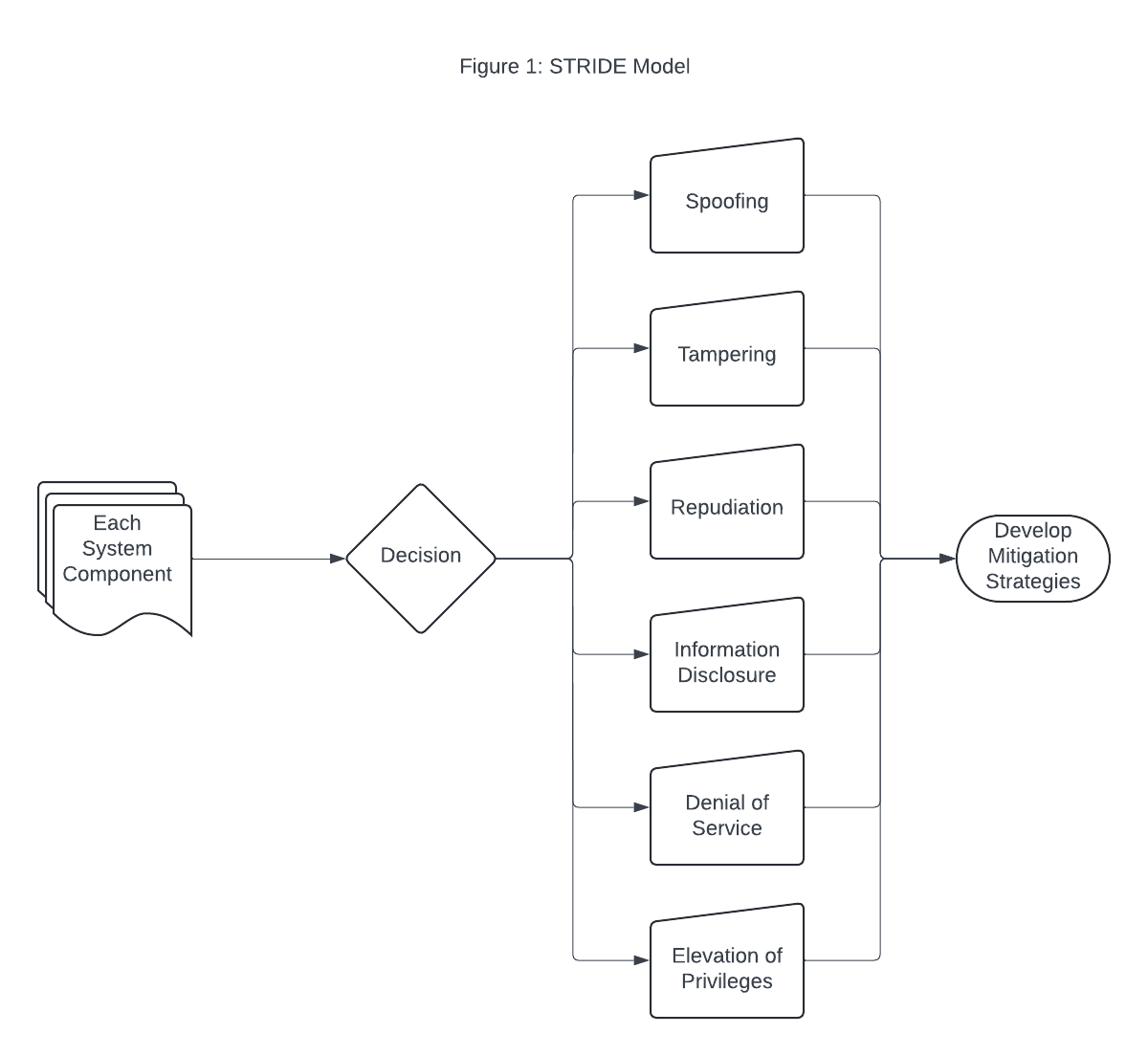
PASTA Model
PASTA was developed in 2012 (Balamurugan et al., 2023) and stands for “Process for Attack Simulation and Threat Analysis” and is made up of the following seven stages: “Define the Objectives,” “Define the Technical Scope,” “Decompose the Application,” “Analyze the Threats,” “Vulnerability Analysis,” “Attack Analysis,” and “Risk and Impact Analysis” (Pape & Mansour, 2024, Section III). This model requires security input from a range of stakeholders, such as people in operations, people in governance, designers, employees responsible for development, etc. (Balamurugan et al., 2023). This model puts risk and potential attackers at the center of the methodology (Balamurugan et al., 2023). The following diagram illustrates the phases of the PASTA model.
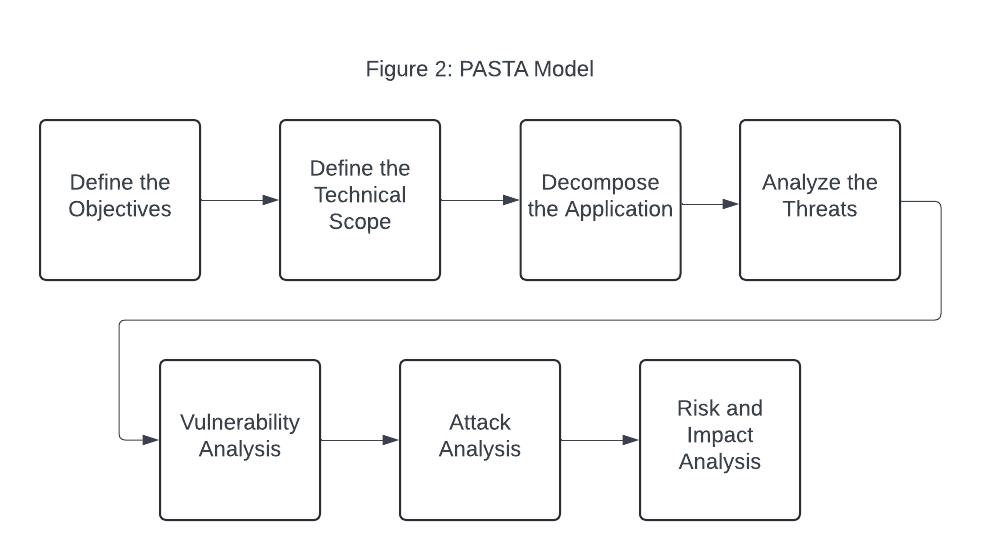
OCTAVE Model
OCTAVE stands for “Operationally Critical Threat, Asset, and Vulnerability Evaluation” (Mackita, 2019, Section 2.1). OCTAVE consists of three main phases: “Build asset-based threat profiles,” “Identify infrastructure vulnerabilities,” and “Develop security strategy and plans” (Mackita, 2019, Section 2.1). Each of these three phases consists of several sub-processes for a total of eight processes (Mackita, 2019). In this model, threats are generally categorized into one of the following four categories: network-based, physical, system, and other (Butcher-Powell, 2006). The process of OCTAVE modeling is illustrated in the following diagram (Alberts et al., 2003).
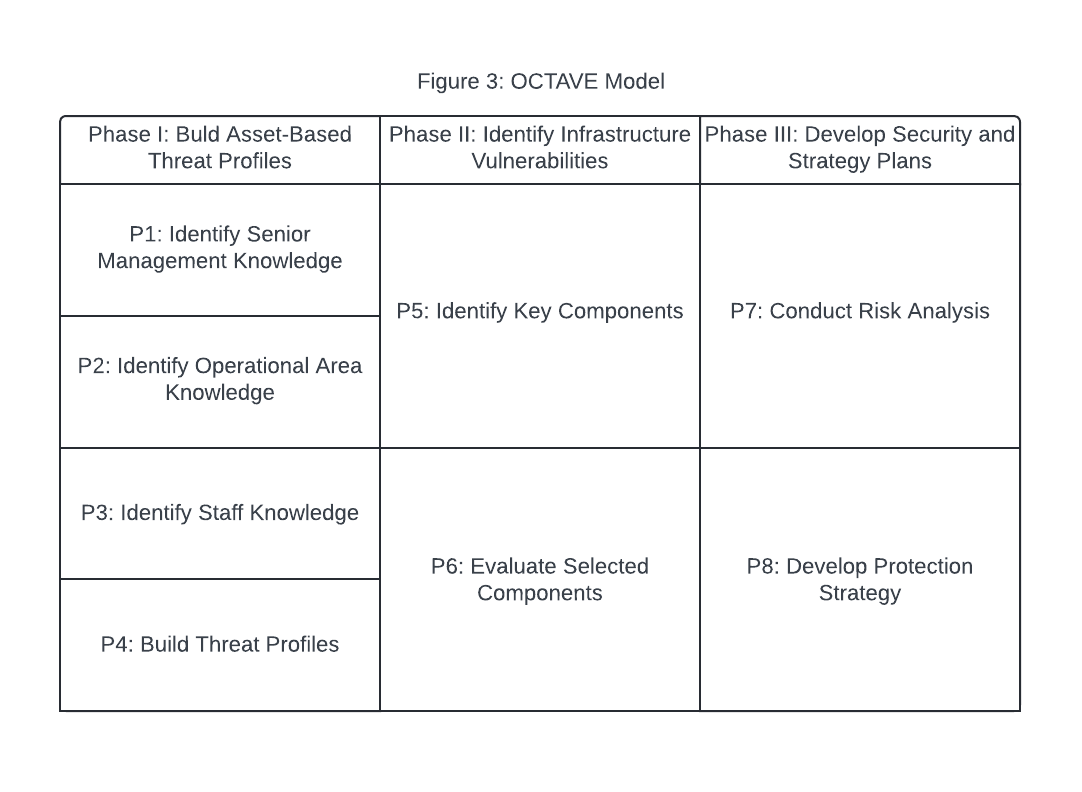
Conclusion
The STRIDE model has been selected due to its track record of being applied in healthcare settings (Ahamad et al., 2022) and its recommendation by the Department of Health and Human Services (2020). Additionally, models such as OCTAVE emphasize risk in relation to IT (Mackita, 2019). While IT risk is an important component to consider, it is not the only threat vector that must be considered for information security in the healthcare sector. The Department of Health and Human Services (2020) recommends several mitigation techniques for each STRIDE category, which are displayed in the following table.
| Figure 4: DHHS Mitigation Techniques | |
|---|---|
| Category | Mitigation Techniques |
| Spoofing | Strong Authentication, Encryption, Cryptographic Protocols |
| Tampering | Strong Authorization, Data Hashing/Signing, Secure Communication Links |
| Repudiation | Secure Audit Trails |
| Information Disclosure | Strong Authorization, Encryption, Secure Communication Links |
| Denial of Service | Not Specified |
| Elevation of Privileges | Proper Authorization Mechanisms, Principle of Least Privilege |
The following table outlines how several other common security risks would be categorized using the STRIDE model:
| Figure 5: Using the STRIDE Model for Common Security Risks | ||
|---|---|---|
| Description | Category | Rating |
| Data Leak: Disgruntled employee leaks confidential patient data | Information Disclosure | High |
| Unauthorized Access: Employee accidentally gains access to patient data | Elevation of Privileges | Low |
| Data Tampering: Authorized employee maliciously changes medical data | Tampering | High |
| Unauthorized Access: Third-party integration is accidentally given increased read access to patient data | Elevation of Privileges | Medium |
References
Ahamad, S. S., Al-Shehri, M., & Keshta, I. (2022). A Secure and Resilient Scheme for Telecare Medical Information Systems With Threat Modeling and Formal Verification. IEEE Access, 10, 120227–120244. https://doi.org/10.1109/ACCESS.2022.3217230
Alberts, C., Dorofee, A., Stevens, J., & Woody, C. (2003). Introduction to the OCTAVE approach. https://doi.org/10.21236/ada634134
Balamurugan, K., Sudalaimuthu, T., & Sherlin Solomi, V. (2023). An analysis of various cyber threat modeling. 2023 Third International Conference on Artificial Intelligence and Smart Energy (ICAIS). https://doi.org/10.1109/icais56108.2023.10073771
Butcher-Powell, L. M. (2006). Better Securing an Infrastructure for Telework. Journal of Cases on Information Technology, 8(4), 71–86. https://doi.org/10.4018/jcit.2006100106
Department of Health and Human Services. (2020). Threat modeling for mobile health systems (No. 202004301030). Retrieved July 20, 2024, from https://www.hhs.gov/sites/default/files/threat-modeling-mobile-health-systems.pdf
Mackita, M., Soo-Young, S., & Tae-Young, C. (2019). ERMOCTAVE: A Risk Management Framework for IT Systems Which Adopt Cloud Computing. Future Internet, 11(9), 195. https://doi.org/10.3390/fi11090195
Pape, N., & Mansour, C. (2024). PASTA threat modeling for vehicular networks security. https://doi.org/10.1109/icict62343.2024.00083
© Trevor French.RSS