Database Security
Introduction
Most organizations need to store and access data in some form. This usually necessitates the need for some sort of database and, consequently, an information security process to accompany it. This article will discuss strategic and technical security measures for good database security and review a security model that will ensure the proper development of databases. Database security models ensure a rigorous security approach is applied to designing, deploying, and utilizing databases.
Database Security
Metrics
There are various security models that one can choose from to protect their databases. Juma and Makupi (2017) suggest that these models should always have metrics and measuring systems associated with them to ensure that security plans are proceeding as desired. More specifically, they suggest that metrics should consider the following three categories of information security: “Foundational defenses and coverage,” “Patch latency,” and “Authentication” (Juma & Makupi, 2017, Section 3.1).
Juma and Makupi (2017) support their suggestion by citing a document from the National Institute of Standards and Technology (NIST) titled “Performance Measurement Guide for Information Security” (NIST, 2008). The NIST document proposes that information security metrics should be measures of impact, measures of effectiveness or efficiency, or measures of implementation (NIST, 2008). NIST also suggests that measures should be repeatable, should be able to inform resourcing decisions, should be developed using data that is available, and should be quantifiable rather than qualitative (NIST, 2008).
Threat Mitigation
Security models should take specific threats and mitigation techniques into consideration. Many threats will be generalizable across various industries and technologies; however, certain industries, tools, and organizations may be exposed to threats that others aren’t. Additionally, constraints on mitigation techniques and acceptable risk levels may vary from organization to organization. In their article titled “A Review of Database Security Concepts, Risks, and Problems,” Teimoor (2021) identifies several common database security threats alongside mitigation techniques. Teimoor (2021) discusses how database privileges can be abused by users being granted too much and by users working within the constraints of their correctly assigned privileges to cause harm. Both of these threats can be mitigated by correctly creating and assigning policies (Teimoor, 2021). Teimoor (2021) also discusses various other threats, such as SQL injection, DoS attacks, and unconstrained exposure to archival data.
Teimoor Model
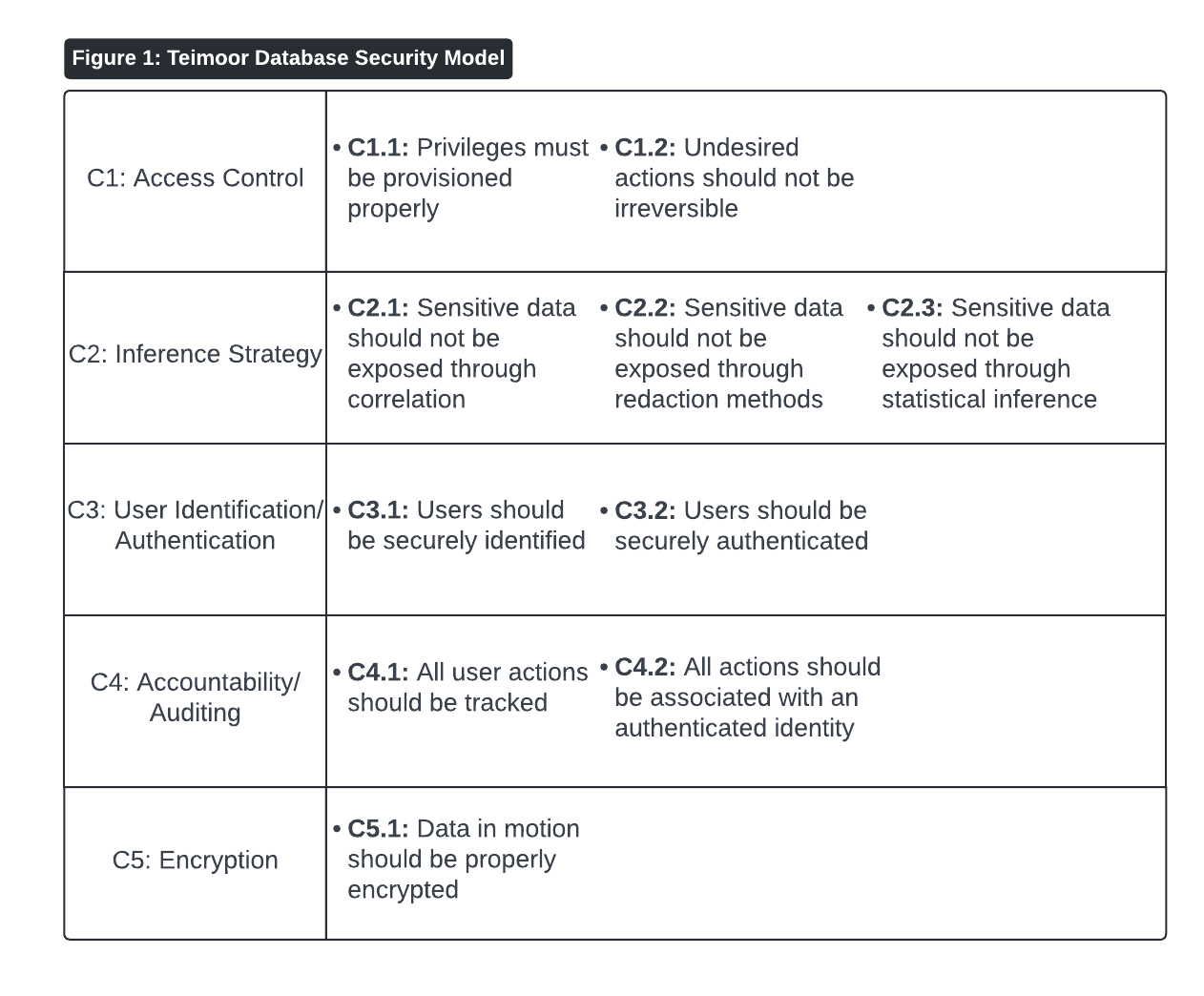
After discussing the literature and various threats pertaining to database security, Teimoor (2021) suggests the following five areas of control that comprise a complete database security model: “Access Control,” “Inference Strategy,” “User Identification/Authentication,” “Accountability and Auditing,” and “Encryption” (Teimoor, 2021, Figure 1).
Figure 1 demonstrates some considerations for each control, as Teimoor (2021) recommended. Access control should include the proper provisioning of database privileges (Teimoor, 2021). Additionally, any undesirable actions should be reversible (Teimoor, 2021). Inference strategy refers to the practice of ensuring sensitive data cannot be discovered through correlated data, statistical inference, or even the redaction techniques themselves (Teimoor, 2021). User identification and authentication refers to ensuring all users are both properly identified and properly authenticated (Teimoor, 2021). Teimoor (2021) suggests that accountability and auditing are enforced by tracking all actions performed in a database and ensuring that each of those actions is tied to an identified and authenticated user. Finally, Teimoor (2021) suggests strong encryption techniques for all data in motion (as opposed to data at rest).
Other Models
Other comprehensive models exist to ensure database security. Additionally, some models are specifically dedicated to single components of database security. For example, access control models exist to ensure all access requests are properly approved or denied (Penelova, 2021). Some examples of access control models include identity-based access control and Role-Based Access Control (RBAC) (Penelova, 2021).
NIST also has many resources on access control models, access control for databases, and the topic of access control itself. Earlier this year, for example, NIST published a report titled “Access Control on NoSQL Databases” (Hu, 2024).
Conclusion
The Teimoor Database Security Model provides a rigorous control framework for the development, deployment, and utilization of databases (Teimoor, 2021). Teimoor (2021) has provided general advice on how each control might be implemented; however, organizations should adapt the model to their use cases by evaluating the threats to their specific organization and the constraints to their mitigation efforts.
In addition to this control framework, users should consider relevant metrics to deploy and track their security efforts to ensure the long-term success of their database security initiative, as recommended by Juma and Makupi (2017). Metrics ensure that one’s selected model's success is continuously evaluated.
Finally, the Teimoor Database Security Model (2021) can be supplemented with models that focus on each of the subcomponents of the comprehensive model.
References
Juma, J., & Makupi, D. (2017). Understanding Database Security Metrics: A review. Mara International Journal of Scientific & Research Publications, 1(1), 40–48. https://core.ac.uk/download/pdf/223128501.pdf
NIST. (2008). Performance Measurement Guide for Information Security: NIST Special Publication 800-55 Revision 1. In NIST.gov. Retrieved August 3, 2024, from https://nvlpubs.nist.gov/nistpubs/legacy/sp/nistspecialpublication800-55r1.pdf
Teimoor, R. A. (2021). A review of database security concepts, risks, and problems. UHD Journal of Science and Technology, 5(2), 38–46. https://doi.org/10.21928/uhdjst.v5n2y2021.pp38-46
Penelova, M. (2021). Access Control Models. Cybernetics and Information Technologies : CIT, 21(4), 77–104. https://doi.org/10.2478/cait-2021-0044
Hu, V. (2024). Access control on NoSQL databases. https://doi.org/10.6028/nist.ir.8504
© Trevor French.RSS